Ethernet MAC Learning¶
The Ethernet bridges are the packet forwarding devices in Ethernet networks. An end device connects to a bridge port with an Ethernet cable from its network interface. Bridges may connect to each other’s ports when longer distance reach is needed. Bridges maintain a layer 2 table for their ports, with MAC address entries learned on specific ports.
Bridge¶
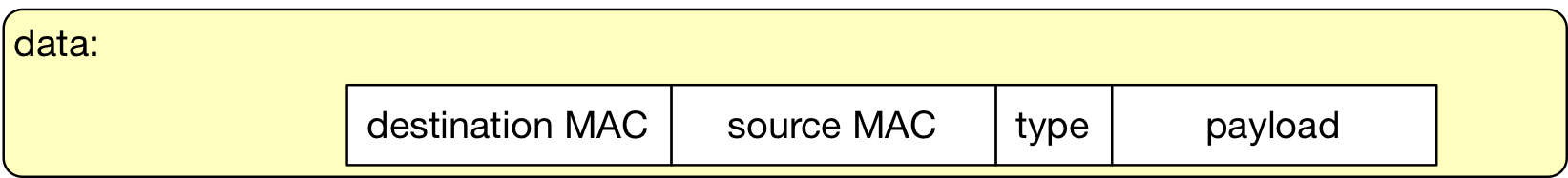
An Ethernet bridge is a network device operating at layer 2: The header of the L2 packet is used to make forwarding decisions by this device, namely, source and destination MAC addresses, and the type of payload the packet is carrying.
An Ethernet bridge is a plug-and-play device that forwards packets according to the records in its layer 2 (L2) table and other forwarding rules available in the Ethernet protocol. The L2 table is indexed by port numbers and each port has MAC address entries. A unique MAC address entry constitutes a row in the L2 table of a bridge which may have many MAC addresses per port listed at a time.
Note
VLANs will be covered in a later section of these learning modules. Each port may have virtual LAN number assignments, depending on the configuration of the bridge.
There is an aging time associated with each MAC address entry that is deleted once the time has expired.
The bridge L2 table rows are the records for each port of the bridge where the values are MAC addresses. These addresses are observed in the source MAC address fields of packets that have been received on bridge ports. An example L2 table for the bridge1 in the figure can be:¶
bridge1 L2 Table |
|||
|---|---|---|---|
Port |
VLAN |
MAC |
Age |
1 |
0 |
aa:aa:bb:bb:13:9f |
48 |
5 |
0 |
28:39:10:82:13:9f |
19 |
5 |
0 |
38:ad:27:34:de:bc |
64 |
Tip
Implementation Insight
The aging time of the entry is updated every time an entry is recorded into the L2 table even if such an entry was already present.
Unique MAC Address Entries
The MAC address entries are unique throughout the bridge L2 table. That is, there cannot be two different ports assigned to the same MAC address. If the same source MAC address is in a packet on a different incoming port than the one that is in the existing L2 table, that entry will be deleted and replaced by the new port number together with the MAC address.
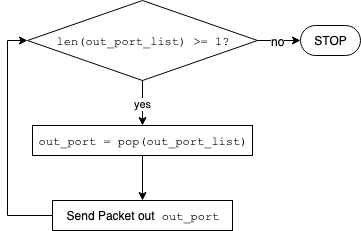
The process flow chart represents how incoming packets are forwarded at Ethernet bridges.
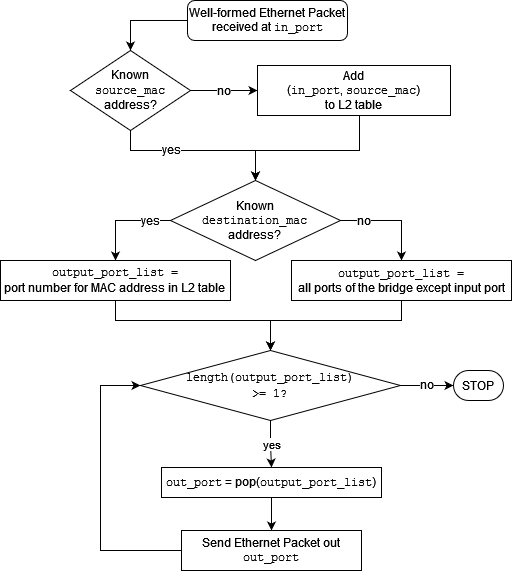
Packet forwarding process in an Ethernet bridge.¶
Bridges (commonly referred to as a switch) have a protocol behavior that can be summarized as:
Listen on all ports continuously
Read the Ethernet header fields of every packet
Make a forwarding decision based on the L2 table records
Forward the packet
The process flow chart governs the behavior of the Ethernet bridge’s MAC learning operation - below is a detailed description of each step. The bridge does not make any changes on the incoming packet while processing it to eventually forward a copy (or copies) or drop. The two main data fields of the packet are the source and destination MAC addresses.
Deep Dive: Ethernet Bridge Behavior
For every incoming packet at bridge ports: Listen to all ports all the time

The packet’s source MAC address is looked up in the L2 table.
[MAC Learning]
If not in the L2 table: record the MAC address for the incoming port
If already in L2 table: continue
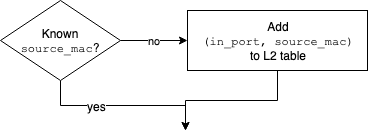
The packet’s destination MAC address is looked up in the L2 table.
[FLOOD]
If not in the L2 table: forward packet on all ports except the incoming port
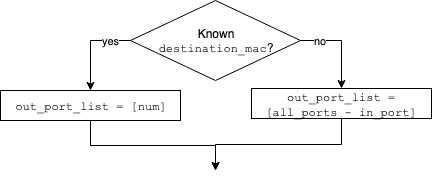
[SELECTIVE SEND]
If there is a match in the L2 table: retrieve the port
If the same as the incoming port: drop the packet
If different: forward to the matching port
Each entry in the table expires at the allocated aging time.
Since bridges record source MAC address of packets that are received on ports, the process is referred to as MAC learning.
Analogy: Learning Names
During an attendance call, the teacher may call out names of students in the class. All others in the class learn their classmates names during this time to later refer to each other with those names. When the teacher does not know who a specific student is, he/she will call that name to the class, in a broadcast fashion, just like the case of flooding in the bridge.
In essence, bridges learn from source MAC address field of packets, and in turn, forward packets based on match of destination MAC address fields with their L2 table: learn from source, forward based on destination.
Analogy: Flood vs Broadcast
During air travel, we experience announcements at airports. An announcement on airport speakers is a broadcast to all people who are inside the airport. The announcement content may have been delivered to the announcement center through one of many means: an airline may have a request to change a gate for a particular flight. The broadcast then happens around that gate area so the message reaches all passengers of that flight so that they can make timely travel to the new gate. The broadcast is not expected to be made back to the airline personnel who requested such an announcement to be made. In this respect, the flood behavior of the bridge is similar to the way broadcast happens: all parties other than the sending party receives the message when bridge forwards to all ports other than the incoming port.
When a packet is addressed to the broadcast MAC address, that is, destination
MAC is FF:FF:FF:FF:FF:FF, Ethernet bridges are programmed to forward this
packet to all of their ports other than the incoming port. In this respect, a
broadcast packet is flooded by the Ethernet bridges. Furthermore, a broadcast
MAC address is never learned by the bridges, that is, if it appears in the source
MAC address field of an Ethernet packet, it is not added to the L2 table.
A Forwarding Scenario¶
Note
Host vs End Device
In these learning modules, end devices refer to all user devices, servers, and other equipment with a network interface that sends and receives messages in a network. The distinction between an end device and a network device is that end devices use the network to send and receive messages whereas network devices enable the users to access remote resources by forwarding the packets sent by end devices. From here on, the learning modules will refer to end devices as hosts to emphasize this distinction. The term host has been historically the name given to end devices at the beginnings of the invention of networks to indicate the capability of hosting user applications and programs on the end devices.
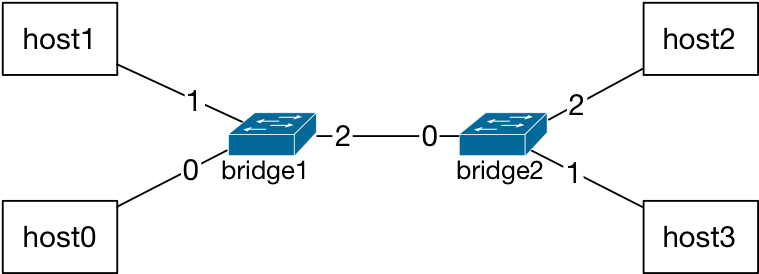
Here is a scenario where host1 is sending a message to host2. Let’s assume that once host2 receives the message, it sends a reply back. Packet from host1 to host2:

Fields in the packet refer to: source MAC = host1 interface MAC and destination MAC = host2 interface MAC¶
The L2 tables at the bridges are empty at the beginning of this scenario.
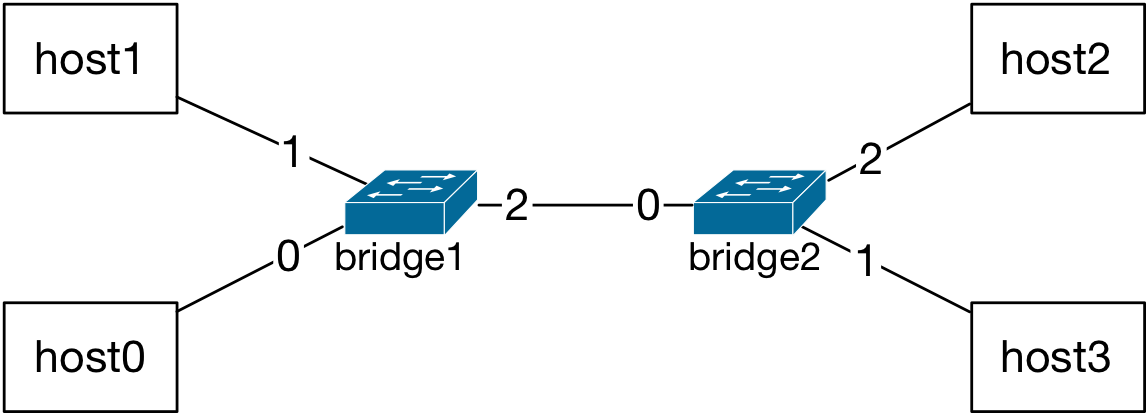
The network graph has two bridges and both L2 tables are empty.¶
bridge1/bridge2 L2 Table |
||
|---|---|---|
Port |
MAC |
Age |
The packet from host1 is received at the port number 1 of bridge1. The MAC address of host1 is not in the L2 table, therefore, the bridge adds this record for port 1 into its L2 table. Next, the bridge looks up the destination MAC address in its L2 table: the MAC address of host2 is not matched to any entry in the L2 table. Therefore, the forwarding decision at bridge1 is to flood: forward packet on ports 0 and 2 (all ports other than the incoming port number 1).
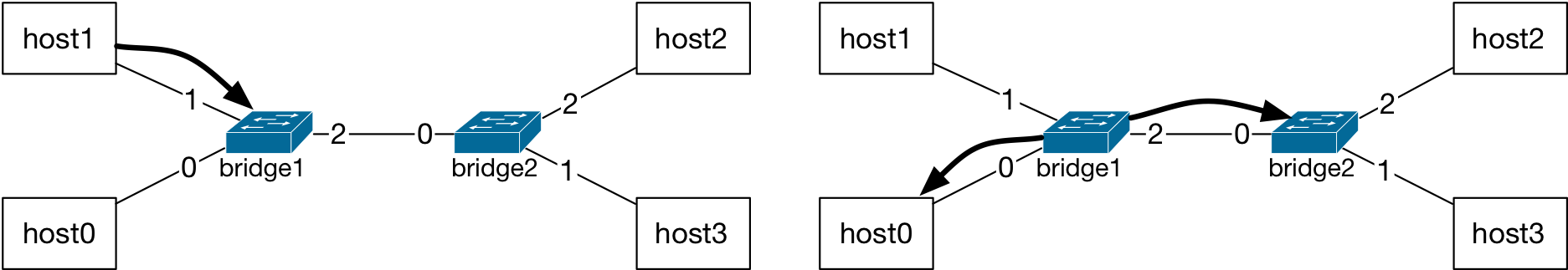
The MAC address of host1 is added to the L2 table for port 1 of bridge1 and the packet is forwarded on ports 0 and 2, that is, flooded.¶
bridge1 L2 Table |
||
|---|---|---|
Port |
MAC |
Age |
1 |
host1_MAC_address |
T1 |
The packet from host1 is received on port 0 of bridge0, and by host0. Since packet’s destination MAC address is not equal to the host0’s network interface address, host0 will drop this packet. And, at bridge2, there are no MAC addresses in the L2 table yet. Therefore, the forwarding decision at bridge2 is also to flood: forward the packet on ports 1 and 2.
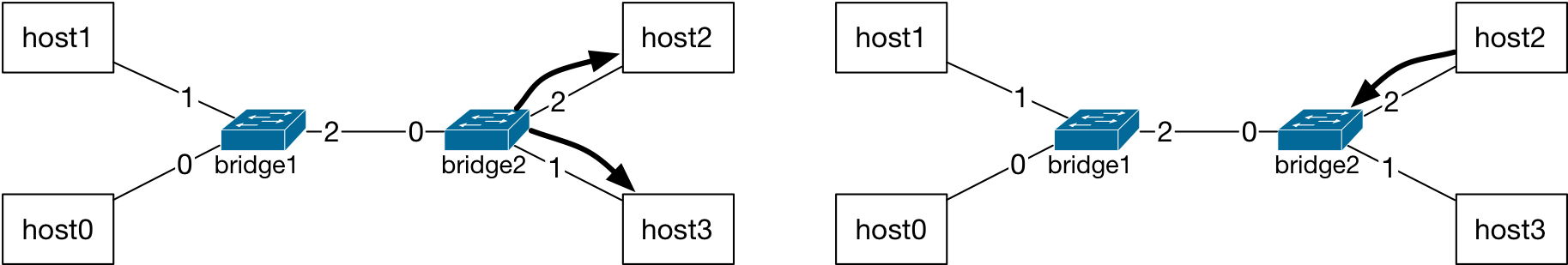
Similarly, at bridge2, packet is forwarded on all ports other than the incoming and host1’s MAC address is added to the L2 table.¶
bridge2 L2 Table |
||
|---|---|---|
Port |
MAC |
Age |
0 |
host1_MAC_address |
T0 |
The packet will be received by host2 and host3: Since the destination MAC address is not the host3’s own MAC address, host3 will drop the packet. Having matched the destination MAC address to its own MAC address, host2 will process this packet.
When host2 sends back a reply, the packet source MAC address, host2’s MAC address, will be recorded on the bridge2 L2 table.

Fields in the packet refer to: source MAC = host2 interface MAC and destination MAC = host1 interface MAC¶
However, this time, bridge2 will match the destination MAC address of this packet, host1’s MAC address, with the entry in its L2 table. Therefore, finding a match for the MAC address during the L2 table lookup, bridge will forward the packet directly to port 0, and not flood. Similarly, bridge1 will also add host2’s MAC address to its L2 table and then directly forward the packet to its port 1.
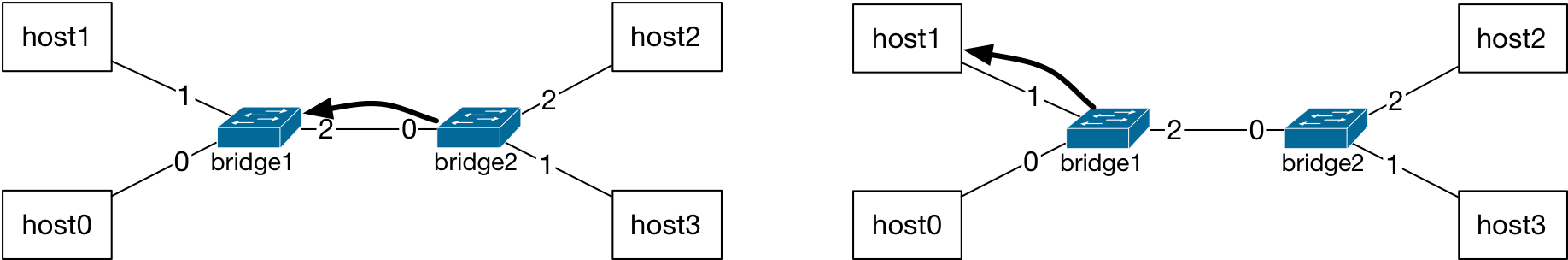
When destination MAC address of the packet is matched to an entry in the L2 table, bridges directly forward the packet to the port listed for that MAC address.¶
bridge1/bridge2 L2 Table |
||
|---|---|---|
Port |
MAC |
Age |
0 |
host1_MAC_address |
T0 |
2 |
host2_MAC_address |
T2 |
Further Reading List
Ethernet standards: http://www.ieee802.org/3/
Interconnections, Second Edition: Bridges, Routers, Switches, and Internetworking Protocols by Radia Perlman, Addison- Wesley, Reading, Mass., 1999, ISBN 0- 201-63448-1.
NEXT
The Ethernet protocol and bridge MAC learning will be observed during the laboratory experiment.