Lab - 2: Internet Protocol and Subnets¶
Objectives¶
The lab is on observations of:
IP packet format
Check the IP address and MAC address of interfaces
Learn about the tool,
ping, that is on IP connectivity
Load Lab Network¶
Use File New
Notebook to open a new notebook.
The labs are conducted using the University of Houston Education python libraries. Load these libraries by executing the following code in the first cell of your lab notebook:
%load_ext uhed
You can now proceed with loading of the lab modules for this class:
%lab
Select your lab topology from the dropdown menu and
then load by clicking the Build Network button.
In order to conduct this lab, please select IP Subnets in the
labpicker dropdowm menu and then click on the Build Network
button.
Topology Orientation¶
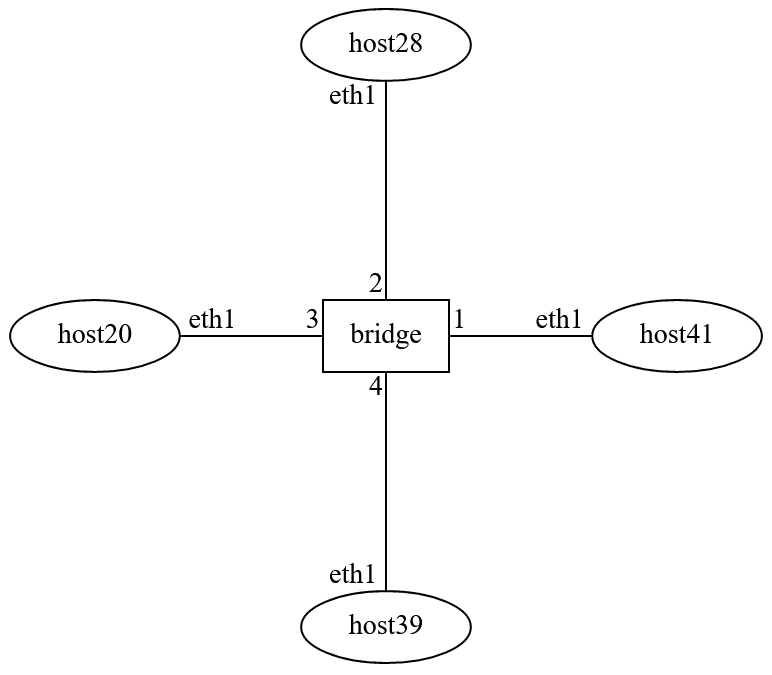
Lab Network Topology¶
Attention
Each time you make a reservation, the hosts will be numbered in a random manner.
Observation Plan and Environment¶
Open a terminal for each host, ssh into the hosts to identify their interfaces.
Examine the subnets provided to you for the lab. Allocate two addresses from each subnet to be assigned to two of your host interfaces in each subnet.
Assign the IP addresses to your host interfaces in your lab notebook:
NET[<hostlabel>].setIPv4Address(<interfacename>, <IPaddress>)
Verify the IP address of the interface of the host by looking at the output of the command:
NET.showInterfaces()
Send packets using
ipsendtool as explained below and monitor the packets using thetcpdumptool at sending and/or receiving hosts.Send an ICMP
echo requestpacket using thepingtool to each IP address of the hosts to observe the IP connectivity.
Example IP Address Allocation and Assignment¶
Retrieve the subnets you have been assigned for this lab. Use the command below:
NET.data["lab-subnets"]
to display the subnets allocated to your lab.
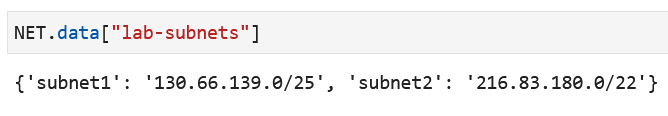
For example,
if the two subnets are 34.137.48.0/22 and 159.43.24.0/23, the
range of IP addresses that are available to assign to a network
interface from each subnet are:
34.137.48.0/22: 34.137.48.1 - 34.137.51.254
159.43.30.0/23: 159.43.30.1 - 159.43.31.254
Attention
The first (min) and last (max) value in these ranges are reserved and not assigned to host interfaces.
The subnet address in each case is:
Subnet address:
34.137.48.0/22Subnet address:
159.43.30.0/23
Tip
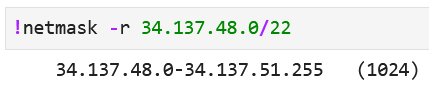
Finding the Range of IP Addresses in a Subnet
Use the tool netmask to display the range of IP addresses
that are available in a given subnet on your lab notebook. Execute:
!netmask -r <subnetaddress>
Where <subnetaddress> is in the form of A.B.C.D/N. For example:
Let’s pick the following assignments to the following host interfaces in this topology:
host03.eth1: 159.43.30.12/23
host12.eth1: 159.43.31.38/23
host34.eth1: 34.137.51.250/22
host35.eth1: 34.137.51.149/22
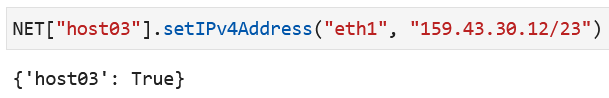
In order to assign these IP addresses, use the notebook commands. For
example, the host03 assignment will be:
NET["host03"].setIPv4Address("eth1", "159.43.30.12/23")
Note
When using the command,
NET[<hostlabel>].setIPv4Address(<interfacename>, <IPaddress>),
the <hostlabel> refers to the label or name you see in the network
topology for that host node, like host03. The <interfacename>
refers to the network interface of the host, typically eth1. Finally,
the <IPaddress> in the command refers to the IP address to be assigned
to the host interface in the format A.B.C.D/N where N refers to the subnet
prefix length.
Network Interfaces: Set & Verify IP Addresses¶
Lab Task
Please run the command NET.showInterfaces() in your lab
notebook to display the node interfaces and their addresses:
An example view from a lab notebook with interface IP and MAC addresses:
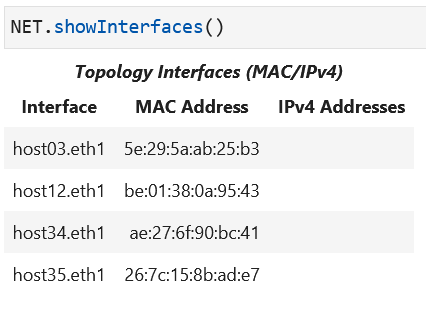
Please note that you can identify the MAC and IP address at the eth1
interface.
Assign an IP address to a host interface using the command to set an IPv4
address: NET[<hostlabel>].setIPv4Address(<interfacename>, <IPaddress>).

Please retrieve the interface information for your topology again to verify that the assigned IP address is now showing up in the displayed table.
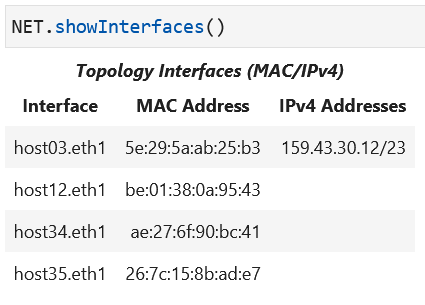
You can also login to the hosts in your topology to examine the interface
addresses using the command ip addr.
For example, in a reservation, here is the output
we have recorded for the command ip addr:
/ # ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7304: eth1@if7303: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc netem state UP qlen 1000
link/ether ae:27:6f:90:bc:41 brd ff:ff:ff:ff:ff:ff
inet 34.137.51.250/22 scope global eth1
valid_lft forever preferred_lft forever
/ #
In this case, the IP address of the host eth1 interface is
34.137.51.250 with a prefix length of 22 for its subnet. The MAC
address of host interface eth1 is ae:27:6f:90:bc:41.
The host interface information (all host interfaces
are called eth1) is tabulated below:
hostname |
Interface MAC |
Interface IP |
|---|---|---|
host03 |
5e:29:5a:ab:25:b3 |
159.43.30.12/23 |
host12 |
be:01:38:0a:95:43 |
159.43.31.38/23 |
host34 |
ae:27:6f:90:bc:41 |
34.137.51.250/22 |
host35 |
26:7c:15:8b:ad:e7 |
34.137.51.149/22 |
Attention
Please repeat the process of identifying subnets, allocating IP addresses to host interfaces and then assigning them to those interfaces for your network now.
ICMP Echo Request: ping Tool¶
At a terminal command line, typing ping A.B.C.D where A.B.C.D is an
IP address, sends ICMP (Internet Control Management Protocol)
echo request packets one after another
to the destination IP address specified as A.B.C.D.
If there is IP connectivity, an echo reply packet will be sent back from
the destination host at the IP address A.B.C.D.
Attention
In order to stop ping from sending packets press
control and c keys at the same time.
The tool provides an output with information on what number of
echo request packets are sent to the destination IP address at
A.B.C.D and some statistics based on the
observed round trip time for these packets.
For example, if you run ping 34.137.53.149
on host command line, meaning interface at host is sending
an echo request to destination host interface IP address of
34.137.53.149, then output is:
/ # ping 34.137.53.149
PING 34.137.53.149 (34.137.53.149) 56(84) bytes of data.
64 bytes from 34.137.53.149: icmp_seq=1 ttl=64 time=1.14 ms
64 bytes from 34.137.53.149: icmp_seq=2 ttl=64 time=0.093 ms
64 bytes from 34.137.53.149: icmp_seq=3 ttl=64 time=0.067 ms
64 bytes from 34.137.53.149: icmp_seq=4 ttl=64 time=0.078 ms
^C
--- 34.137.53.149 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3044ms
rtt min/avg/max/mdev = 0.067/0.345/1.145/0.462 ms
/ #
When ^C stops the ping a statistic is displayed. For example,
in this case there were four packets sent and received by host17 because
the host with interface IP 34.137.53.149 replied with echo reply
to host17 interface (which had the interface IP address of 34.137.55.250
which is in the same subnet with the destination interface IP address).
Total time of running ping was three seconds (3044 msec to be exact!).
The round trip time (RTT) statistics are in the
last line with minimum, average, maximum, and minimum standard deviation
calculated from the measurements:
...
--- 34.137.53.149 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3044ms
rtt min/avg/max/mdev = 0.067/0.345/1.145/0.462 ms
If the same host, host34, were to send echo request to an IP address
in a different
subnet range than its own own IP address, for example, to host03
interface IP address, 159.43.30.12, the result is:
/ # ping 159.43.30.12
PING 159.43.30.12 (159.43.30.12) 56(84) bytes of data.
From 34.137.51.250 icmp_seq=1 Destination Host Unreachable
From 34.137.51.250 icmp_seq=2 Destination Host Unreachable
From 34.137.51.250 icmp_seq=3 Destination Host Unreachable
^C
--- 159.43.30.12 ping statistics ---
5 packets transmitted, 0 received, +3 errors, 100% packet loss, time 4078ms
IP Packets: ipsend Tool¶
Using the command line interface on a host in your topology, you can
specify all header fields of an IP packet. The
tool allows you to send arbitrary IP protocol packets from your
host interfaces.
The
arguments of the tool can be retrieved by running the command
with the --help option:
# ipsend --help
usage: /usr/bin/ipsend [-h] [--dst-mac DSTMAC] [--src-mac SRCMAC]
[--eth-type ETHTYPE] [--vlan VLAN]
[--eth-payload ETHPAYLOAD] [--dst-ip DSTIP]
[--src-ip SRCIP] [--protocol PROTOCOL]
[--ip-payload IPPAYLOAD]
intf
positional arguments:
intf Host interface to send on
optional arguments:
-h, --help show this help message and exit
--dst-mac DSTMAC Sending an Ethernet packet to a destination MAC
address
--src-mac SRCMAC Source MAC address
--eth-type ETHTYPE Ethernet type
--vlan VLAN Packet VLAN ID
--eth-payload ETHPAYLOAD
--dst-ip DSTIP Sending an IP packet to a destination IP address
--src-ip SRCIP Specify source address of IP packet
--protocol PROTOCOL Specify the layer 4 protocol in IP payload
--ip-payload IPPAYLOAD
Monitor Packet Captures at Network Interfaces: tcpdump Tool¶
The packet that is sent on an interface of a host can be observed using the tcpdump
tool at the host command line. The output of tcpdump will show the packets that are
sent and received on the interface specified in its arguments. More information about the
command line tool can be found on
tcpdump man page
The tcpdump command arguments that are used in the labs are:
specify the interface to monitor using
-i eth1argument,show ethernet frames using
-eargument,omit name resolution using
-nargument,display payload using
-Aargument,filter out the frames destined to the reserved MAC address for STP (Spanning Tree Protocol),
01:80:c2:00:00:00, to reduce the displayed traffic on terminal screen usingnot ether dst 01:80:c2:00:00:00,filter out the packets that carry any IPv6 protocol payloads by excluding the specific Ethertype value for IPv6:
not ether proto 0x86dd:# tcpdump -i eth1 -Ane not ether dst 01:80:c2:00:00:00 and not ether proto 0x86ddWhen executed, the screen will show:
# tcpdump -i eth1 -Ane not ether dst 01:80:c2:00:00:00 and not ether proto 0x86dd tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
The output of the command shows that ethernet packets are being listened to on
the eth1 interface.
Attention
In order to stop tcpdump from displaying packets captured,
press the control and c keys at the same time on your keyboard. When
the program stops running, it will display a summary at the output and your
command line shell will appear:
/ # tcpdump -i eth1 -Ane not ether dst 01:80:c2:00:00:00 and not ether proto 0x86dd
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
16:41:52.101651 86:7d:67:90:a1:6b (oui Unknown) > aa:bb:cc:dd:ee:8a (oui Unknown), ethertype Unknown (0x0820), length 19:
0x0000: 6865 6c6c 6f hello
hello
^C
1 packet captured
1 packet received by filter
0 packets dropped by kernel
/ #
If a packet count has been specified in the
command argument list by using -c option (for example, -c 5 to capture 5 packets), the
tcpdump process will exit automatically when the total specified number of packets are
captured and displayed.
Learning Activities¶
Step 1
Use the provided subnets to allocate and then assign IP addresses to
your host interfaces. Verify your address assignments using the output
of NET.showInterfaces() output in your notebook.
Step 2
Use the command line tool called ping to send
echo request packets to check their IP connectivity status.
2a. ssh into hosts in the topology and use ping at the command line
to send an ICMP echo request within the subnet of the sending host.
2b. ssh into the same host where you are using the command ping to also
monitor the packets being sent and received by the host,
monitor packets using tcpdump using the command below:
tcpdump -i eth1 -Ane not ether dst 01:80:c2:00:00:00 and not ether proto 0x86DD
2c. Observations:
Which hosts are connected at layer 3?
How does subnet addressing relate to layer 3 connectivity?
Step 3 – Lab2 Homework Submission
STOP! Did you practice this week’s material using the %practice facility in your notebook?
Please solve the question(s) and make sure to receive a Correct! response in all questions
before you attempt to submit your assignment.
There are two steps to complete your assignment:
1. In your lab notebook, run:
%homeworkto complete and submit this portion.
2. In your notebook, run:
%exerciseto solve the question(s) and submit this portion.